Torrents have become very popular way to download everything for free of cost like Movies, Games, Software, Music, Scripts etc. Torrents are everywhere on the internet with some advantages and disadvantages, here we will briefly try to explain what actually torrents are and how they work.
Torrent actually itself is a small file having
*.torrent extension, that you can say it contains a link to the file to be downloaded. But here in this case, files to be downloaded are not hosted on web servers instead these files are downloaded from other computers (just like yours) connected with internet.
In simpler words, if you have downloading a file from torrent, same you are providing to download for other downloader and similarly you can download files shared by other internet users.
Key terms of this service are Seeder, Leecher, Peer, Tracker, Open Tracker, and Private Tracker etc.
Seeder is actually the first person who shares the file for download and Leecher is one who downloads the file. While combining both the terms is named as a peer. As leecher gets his downloading completed he also becomes a seeder and starts uploading the same file whenever it is requested by any other leecher, while he also uploads when he is downloading but as that time he is a peer.
Tracker is the soul of Bit Torrent protocol. A tracker is actually a server which monitors the data to be transferred between peers. It has nothing to do with what they are uploading and downloading because those files are not hosted on that server but still it is a counter plus link between peers. Another difference is that it uses a principal called tit-for-tat. This means that in order to receive files, you have to give them.
Counter in a sense that it measures how much data a user has downloaded and uploaded. On the other hand it is a link, as these days almost all sites have developed their own trackers. When a torrent is uploaded on some site, and user download torrent file to download the original torrent content, tracker automatically adds a Tracker URL also known as Passkey in that file, which is used to track the data transferred. This passkey is unique for each user so tracker individually monitors each and every user’s stats.
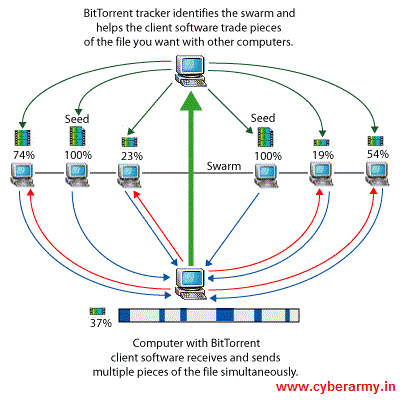
One of the most effective feature of a torrent is that, if there are 10 seeders for the same file, worldwide, you can download from all of them at the same time, meaning that you will get one part of the file from one seeder and the other one from someone else. This goes on and when you are completed you get the original file.
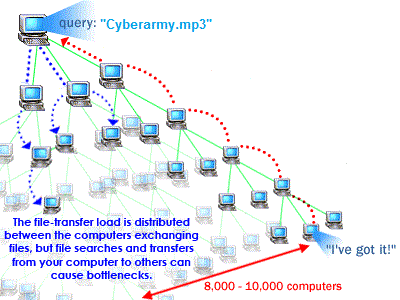
It follows a different method of sharing files known as Peer-Peer Sharing Peer-to-peer file sharing is different from traditional file downloading. In peer-to-peer sharing, you use a software program (rather than your Web browser) to locate computers that have the file you want. Because these are ordinary computers like yours, as opposed to servers, they are called peers. The process works like this:
• You run peer-to-peer file-sharing software (for example, a Gnutella program) on your computer and send out a request for the file you want to download.
• To locate the file, the software queries other computers that are connected to the Internet and running the file-sharing software.
• When the software finds a computer that has the file you want on its hard drive, the download begins.
• Others using the file-sharing software can obtain files they want from your computer’s hard drive.
The file-transfer load is distributed between the computers exchanging files, but file searches and transfers from your computer to others can cause bottlenecks. Some people download files and immediately disconnect without allowing others to obtain files from their system, which is called leeching. This limits the number of computers the software can search for the requested file.
Open and Private trackers are also very important these days, on some sites they have set
RATIO RESTRICTIONS. Ratio restrictions are actually to force the user to upload for others as he has downloaded something for himself.
Private trackers are for this purpose, most of the sites have private trackers and user needs to register there, to download. While in case of open tracker, you just download the torrent and your files, they do not force you to maintain the download/upload ratio.
One of the popular Open trackers is that of ThePirateBay.org, they have millions and millions of seeders and leechers and they count download upload but still you can download torrent even without registration so they count stats on their own. While that of Private Tracker is IPTorrent.com. There are a lot of popular torrent sites which have huge amount of torrents, some of them are open and most are private ones:
• MiniNova.org
• Demonoid.com
• IsoHunt.com
• YouTorrent.com
• SumoTorrent.com
• BwTorrents.com
In a nut shell, main difference between and open and private tracker is that, to download a torrent from a site having private tracker, you need to be registered there and in case of open tracker that is not needed. And Private Tracker sites force you to maintain the ratio by uploading too otherwise they ban your account and in open tracker you are not asked to upload and to maintain your ratio.
But, private trackers are more reliable and effective as they are being run on big servers with constant monitoring. Most of the private trackers have faster speeds and safer downloads. Private trackers implement a strict set of rules, so generally files containing malware are extremely uncommon. Many private trackers keep in close contact with each other, so bad users (who trade invites or attempt to fake their ratio) can be quickly blacklisted. Almost all private trackers implement a passkey system, which is a key tool to measure stats of a user as well as to point out him in case of any wrong attempt made by him.
At the moment one can say that you can find everything on torrents, even those which are impossible to find as direct downloads. Torrents are becoming very popular day by day but still they are marked as illegal. Even though this service itself is not illegal but the content shared is illegal.
Torrent itself is not illegal, File sharing is not a crime, but its use makes it illegal because of piracy issues.





